Easy Passage through the Cisco ICND1 100-105 exam is not an easy task.
HEROESXIII offers 40 of the latest effective Cisco ICND1 100-105 exam dumps convenient for you to practice online,
100-105 pdf free download to help you improve your skills. Still looking for a Cisco 100-105 certification exam dump?
https://www.geekcert.com/100-105.html helps you easily prepare for exams in the shortest possible time,
geekcert update your learning guidance materials throughout the year, Helps you pass the exam easily.
Click in and you can learn the latest ICND1 dumps in PDF and VCE documents.
[PDF] Free Cisco 100-105 dumps download from Google Drive: https://drive.google.com/open?id=1Yphc4c8ePWuVhB0QYmskoxqM_3guN6bv
[PDF] Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1dq6fv9FX6zSDDoHc3ge-WzVU9SNaUbsH
100-105 ICND1 – Cisco: https://www.cisco.com/c/en/us/training-events/training-certifications/exams/current-list/100-105-icnd1.html
geekcert offers the latest Cisco 100-105 practice test free of charge (40Q&As)
QUESTION 1
Which feature allows a device to use a switch port that is configured for half-duplex to access the network?
A. CSMA/CD
B. IGMP
C. port security
D. split horizon
Correct Answer: A
Explanation
Explanation/Reference:
Ethernet began as a local area network technology that provided a half-duplex shared channel for stations connected to coaxial cable segments linked with signal repeaters. In this appendix, we take a detailed look at the half-duplex shared-
channel mode of operation, and at the CSMA/CD mechanism that makes it work.
In the original half-duplex mode, the CSMA/CD protocol allows a set of stations to compete for access to a shared Ethernet channel in a fair and equitable manner. The protocol’s rules determine the behavior of Ethernet stations, including
when they are allowed to transmit a frame onto a shared Ethernet channel, and what to do when a collision occurs. Today, virtually all devices are connected to Ethernet switch ports over full-duplex media, such as twisted-pair cables. On this
type of connection, assuming that both devices can support the full-duplex mode of operation and that Auto-Negotiation (AN) is enabled, the AN protocol will automatically select the highest-performance mode of operation supported by the
devices at each end of the link. That will result in full-duplex mode for the vast majority of Ethernet connections with modern interfaces that support full duplex and AN.
QUESTION 2
Which statement about the inside interface configuration in a NAT deployment is true?
A. It is defined globally
B. It identifies the location of source addresses for outgoing packets to be translated using access or route maps.
C. It must be configured if static NAT is used
D. It identifies the public IP address that traffic will use to reach the internet.
Correct Answer: B
Explanation
Explanation/Reference:
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about the benefits of configuring NAT
for IP address conservation. NAT enables private IP internetworks that use nonregistered IP addresses to connect to the Internet. NAT operates on a device, usually connecting two networks, and translates the private (not globally unique)
addresses in the internal network into legal addresses before packets are forwarded onto another network. NAT can be configured to advertise to the outside world only one address for the entire network. This ability provides additional
security by effectively hiding the entire internal network behind that one address. NAT is also used at the enterprise edge to allow internal users access to the Internet and to allow Internet access to internal devices such as mail servers.
QUESTION 3
Which value is indicated by the next hop in a routing table?
A. preference of the route source
B. IP address of the remote router for forwarding the packets
C. how the route was learned
D. exit interface IP address for forwarding the packets
Correct Answer: D
Explanation
Explanation/Reference:
The routing table contains network/next hop associations. These associations tell a router that a particular destination can be optimally reached by sending the packet to a specific router that represents the “next hop” on the way to the final
destination. The next hop association can also be the outgoing or exit interface to the final destination.
QUESTION 4
Which route source code represents the routing protocol with a default administrative distance of 90 in the routing table?
A. S
B. E
C. D
D. R
E. O
Correct Answer: C
Explanation
Explanation/Reference:
SStatic
EEGP
DEIGRP
RRIP
OOSPF
Default Administrative distance of EIGRP protocol is 90 then answer is C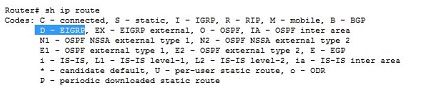
Default Distance Value TableThis table lists the administrative distance default values of the protocols that Cisco supports:
Route Source
Default Distance Values
Connected interface
Static route
Enhanced Interior Gateway Routing Protocol (EIGRP) summary route External Border Gateway Protocol (BGP)
Internal EIGRP
IGRP
OSPF
Intermediate System-to-Intermediate System (IS-IS) Routing Information Protocol (RIP)
Exterior Gateway Protocol (EGP)
On Demand Routing (ODR)
External EIGRP
Internal BGP
Unknown*
QUESTION 5
![]()
Refer to the exhibit. Which feature is enabled by this configuration?
A. static NAT translation
B. a DHCP pool
C. a dynamic NAT address pool
D. PAT
Correct Answer: C
Explanation
QUESTION 6
Which statement about a router on a stick is true?
A. Its date plane router traffic for a single VI AN over two or more switches.
B. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs on the same subnet.
C. It requires the native VLAN to be disabled.
D. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs.
Correct Answer: D
Explanation
Explanation/Reference:
https://www.freeccnaworkbook.com/workbooks/ccna/configuring-inter-vlan-routing-router- on-a-stick
QUESTION 7
Refer to the exhibit. The network administrator must complete the connection between the RTA of the XYZ Company and the service provider. To accomplish this task, which two devices could be installed at the customer site to provide a
connection through the local loop to the central office of the provider? (Choose two.)
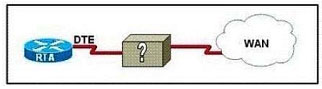
A. WAN switch
B. PVC
C. ATM switch
D. multiplexer
E. CSU/DSU
F. modem
Correct Answer: EF
Explanation
QUESTION 8
Which adverse situation can occur if an Ethernet cable is too long?
A. late collisions
B. giants
C. interface resets
D. runts
Correct Answer: A
Explanation
QUESTION 9
Refer to the exhibit.
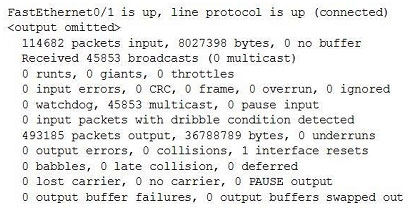
Which two of the output fields could help you determine if a broadcast storm has occurred? (Choose two.)
A. giants
B. no buffer
C. collisions
D. ignored
E. dribble condition
Correct Answer: BD
Explanation
QUESTION 10
Configuration of which option is required on a Cisco switch for the Cisco IP phone to work?
A. PortFast on the interface
B. the interface as an access port to allow the voice VLAN ID
C. a voice VLAN ID in interface and global configuration mode
D. Cisco Discovery Protocol in global configuration mode
Correct Answer: B
Explanation
Explanation/Reference:
Explanation: Explanation
When you connect an IP phone to a switch using a trunk link, it can cause high CPU utilization in the switches. As all the VLANs for a particular interface are trunked to the phone, it increases the number of STP instances the switch has to
manage. This increases the CPU utilization. Trunking also causes unnecessary broadcast / multicast / unknown unicast traffic to hit the phone link.
In order to avoid this, remove the trunk configuration and keep the voice and access VLAN configured along with Quality of Service (QoS). Technically, it is still a trunk, but it is called a Multi-VLAN Access Port (MVAP). Because voice and
data traffic can travel through the same port, you should specify a different VLAN for each type of traffic. You can configure a switch port to forward voice and data traffic on different VLANs. Configure IP phone ports with a voice VLAN
configuration. This configuration creates a pseudo trunk, but does not require you to manually prune the unnecessary VLANs. The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. You can configure a voice
VLAN with the “switchport voice vlan …” command under interface mode. The full configuration is shown below:
Switch(config)#interface fastethernet0/1
Switch(config-if)#switchport mode access
Switch(config-if)#switchport access vlan 10
Switch(config-if)#switchport voice vlan 20
Reference: http://www.cisco.com/c/en/us/support/docs/switches/catalyst-4500-series- switches/69632-configuring-cat-ip-phone.html
Configure the Switch Port to Carry Both Voice and Data TrafficWhen you connect an IP phone to a switch using a trunk link, it can cause high CPU utilization in the switches. As all the VLANs for a particular interface are trunked to the phone,
it increases the number of STP instances the switch has to manage. This increases the CPU utilization. Trunking also causes unnecessary broadcast / multicast / unknown unicast traffic to hit the phone link.
In order to avoid this, remove the trunk configuration and keep the voice and access VLAN configured along with Quality of Service (QoS). Technically, it is still a trunk, but it is called a Multi-VLAN Access Port (MVAP). Because voice and
data traffic can travel through the same port, you should specify a different VLAN for each type of traffic. You can configure a switch port to forward voice and data traffic on different VLANs. Configure IP phone ports with a voice VLAN
configuration. This configuration creates a pseudo trunk, but does not require you to manually prune the unnecessary VLANs.
The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. The voice VLAN feature is disabled by default. The Port Fast feature is automatically enabled when voice VLAN is configured. When you disable voice
VLAN, the Port Fast feature is not automatically disabled.
QUESTION 11
An administrator issues the show ip interface s0/0 command and the output displays that interface Serial0/0 is up, line protocol is up What does “line protocol is up” specifically indicate about the interface?
A. The cable is attached properly.
B. CDP has discovered the connected device.
C. Keepalives are being received on the interface.
D. A carrier detect signal has been received from the connected device.
E. IP is correctly configured on the interface.
Correct Answer: C
Explanation
QUESTION 12
Which command is used to build DHCP pool?
A. ipdhcp conflict
B. ipdhcp-server pool DHCP
C. ipdhcp pool DHCP
D. ipdhcp-client pool DHCP
Correct Answer: C
Explanation
QUESTION 13
Refer to the exhibit.
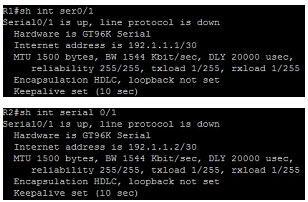
A network technician is unable to ping from R1 to R2. What will help correct the problem?
A. Ensure that the serial cable is correctly plugged in to the interfaces.
B. Apply the clock rate 56000 configuration command to the serial0/1 interface of R1.
C. Configure the serial0/1 interfaces on R1 and R2 with the no shutdown command.
D. Change the address of the serial0/1 interface of R1 to 192.1.1.4.
E. Change the subnet masks of both interfaces to 255.255.255.240.
Correct Answer: A
Explanation
QUESTION 14
Which command can you enter to verify that a 128-bit address is live and responding?
A. traceroute
B. telnet
C. ping
D. ping ipv6
Correct Answer: C
Explanation
QUESTION 15
Which port-security feature allows a switch to learn MAC addresses dynamically and add them to the running configuration?
A. security violation restrict mode
B. switch port protection
C. sticky learning
D. security violation protect mode
Correct Answer: C
Explanation
Explanation/Reference:
You can configure an interface to convert the dynamic MAC addresses tosticky secure MAC addresses and to add them to the running configuration by enabling sticky learning. To enable sticky learning, enter the switchport port-security mac-
address sticky interface configuration command. When you enter this command, the interface converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky
secure MAC addresses.
QUESTION 16
Which transport layer protocol is best suited for the transport of VoIP data?
A. RIP
B. UDP
C. TCP
D. OSPF
E. HTTP
Correct Answer: B
Explanation
QUESTION 17
CORRECT TEXT
How do you bypass password on cisco device?
A. Change the configuration register to 0x2142. With this setting when that router reboots, it bypasses the startup-config and no password is required.
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 18
Refer to the exhibit.
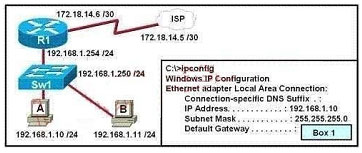
What value should be displayed in Box 1 of the ipconfig output of host A?
A. 172.18.14.5
B. 172.18.14.6
C. 192.168.1.10
D. 192.168.1.11
E. 192.168.1.250
F. 192.168.1.254
Correct Answer: F
Explanation
Explanation/Reference:
QUESTION 19
In which two ways does TCP differ from UDP? (Choose two.)
A. TCP segments are essentially datagrams.
B. TCP uses broadcast delivery.
C. TCP provides sequence numbering of packets.
D. TCP provides synchronized communication.
E. TCP provides best effort delivery.Correct Answer: CD
Explanation
Explanation/Reference:
Explanation: http://www.diffen.com/difference/TCP_vs_UDP Before two computers can communicate over TCP, they must synchronize their initial sequence numbers (ISN)
TCP uses a sequence number to identify each byte of data. The sequence number identifies the order of the bytes sent from each computer so that the data can be reconstructed in order, regardless of any fragmentation, disordering, or
packet loss that may occur during
QUESTION 20
What is true about ipv6 unique local addresses:
A. Global id
B. Public routable
C. Summarization
D. Unique prefix
Correct Answer: D
Explanation
QUESTION 21
Scenario:
You are a junior network engineer for a financial company, and the main office network is experiencing network issues. Troubleshoot the network issues. Router R1 connects the main office to the internet, and routers R2 and R3 are internal
routers.
NAT is enabled on router R1.
The routing protocol that is enabled between routers R1, R2 and R3 is RIPv2.
R1 sends the default route into RIPv2 for the internal routers to forward internet traffic to R1.
You have console access on R1, R2 and R3 devices. Use only show commands to troubleshoot the issues
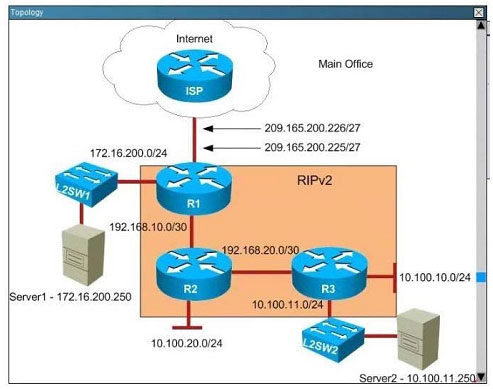
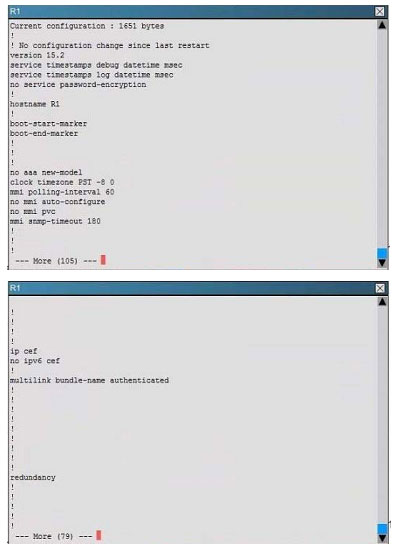
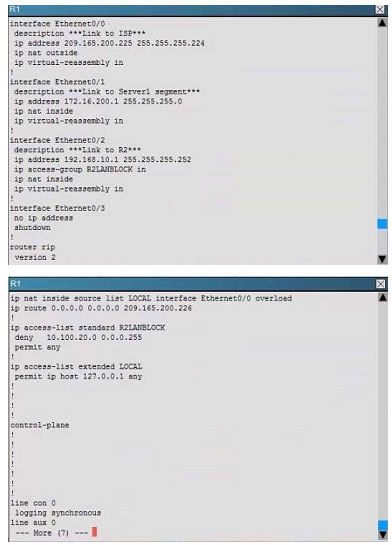

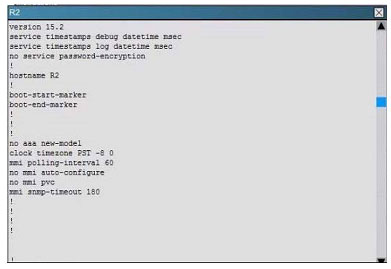
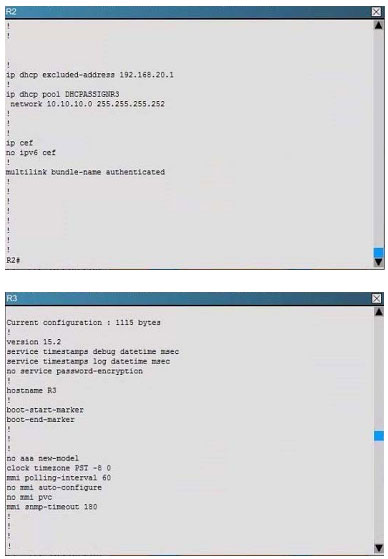
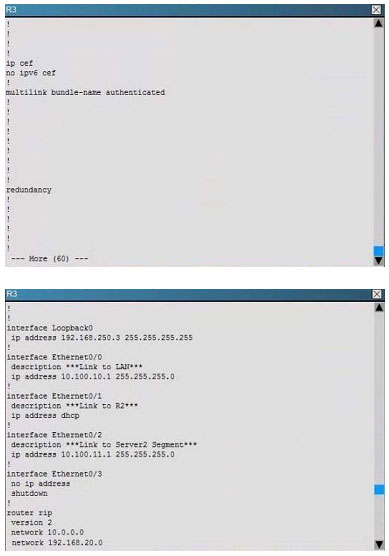
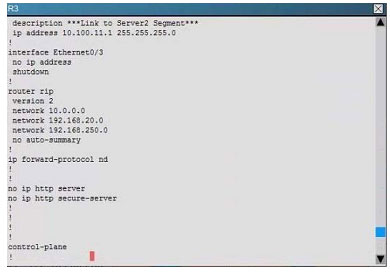
Users complain that they are unable to reach internet sites. You are troubleshooting internet connectivity problem at main office. Which statement correctly identifies the problem on Router R1?
A. Interesting traffic for NAT ACL is incorrectly configured.
B. NAT configurations on the interfaces are incorrectly configured
C. NAT translation statement incorrectly configured.
D. Only static NAT translation configured for the server, missing Dynamic NAT or Dynamic NAT overloading for internal networks.
Correct Answer: B
Explanation
QUESTION 22
Which function enables an administrator to route multiple VLANs on a router?
A. IEEE 802 1X
B. HSRP
C. port channel
D. router on a stick
Correct Answer: D
Explanation
QUESTION 23
Which feature automatically disables Cisco Express Forwarding when it is enabled?
A. multicast
B. IP redirects
C. RIB
D. ACL logging
Correct Answer: D
Explanation
Explanation/Reference:
If you enable CiscoExpress Forwarding and then create an access list that uses the logkeyword, the packets that match the access list are not Cisco Express Forwarding switched. They are process switched. Logging disables Cisco Express
Forwarding.
QUESTION 24
When troubleshooting a LAN interface operating in full duplex mode, which error condition can be immediately ruled out?
A. giants
B. no buffers
C. collisions
D. ignored
E. dribble condition
Correct Answer: C
Explanation
QUESTION 25
Refer to the exhibit.
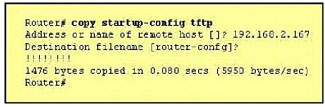
What does the address 192.168.2.167 represent?
A. the TFTP server from which the file startup-config is being transferred
B. the router from which the file startup-config is being transferred
C. the TFTP server from which the file router-confg is being transferred
D. the TFTP server to which the file router-confg is being transferred
E. the router to which the file router-confg is being transferred
F. the router to which the file startup-config is being transferred
Correct Answer: D
Explanation
QUESTION 26
Scenario:You work for a company that provides managed network services, and of your real estate clients running a small office is experiencing network issues, Troubleshoot the network issues.
Router R1 connects the main office to internet, and routers R2 and R3 are internal routers
NAT is enabled on Router R1.
The routing protocol that is enable between routers R1, R2, and R3 is RIPv2.
R1 sends default route into RIPv2 for internal routers to forward internet traffic to R1.
Server1 and Server2 are placed in VLAN 100 and 200 respectively, and dare still running router on stick configuration with router R2.
You have console access on R1, R2, R3, and L2SW1 devices. Use only show commands to troubleshoot the issues.
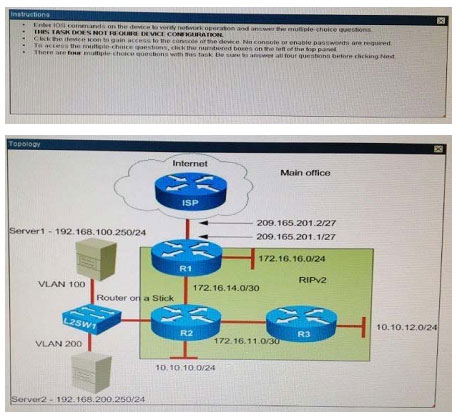

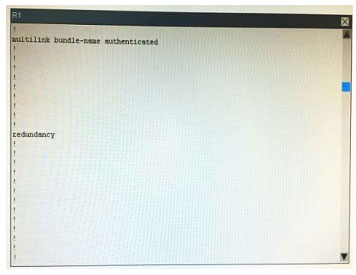
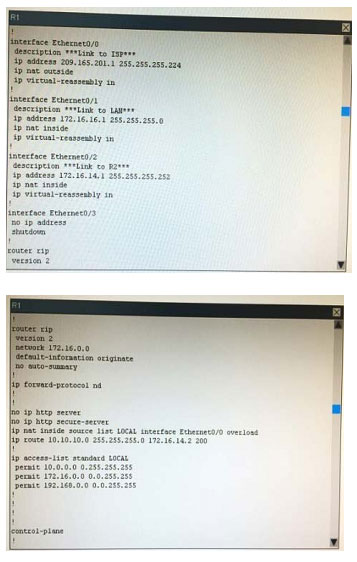
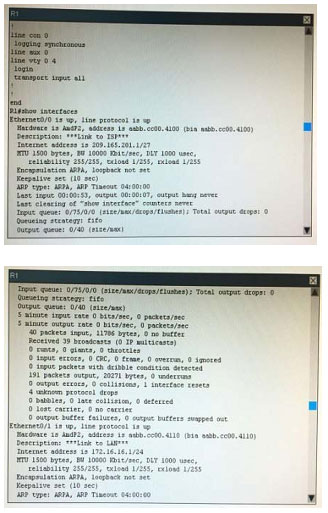
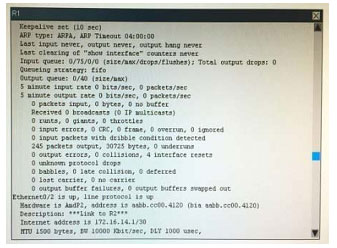
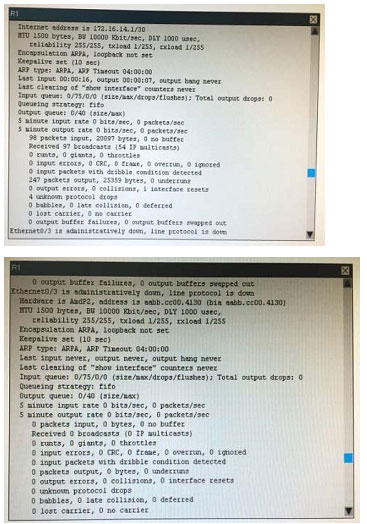
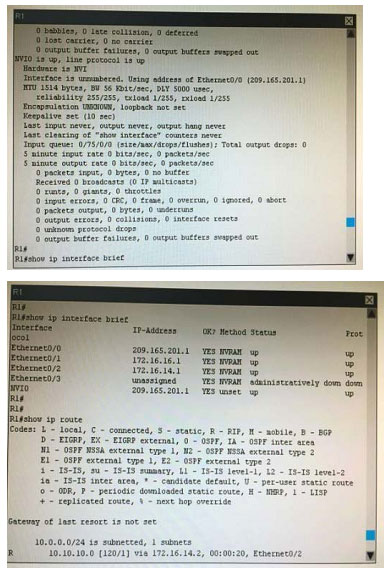
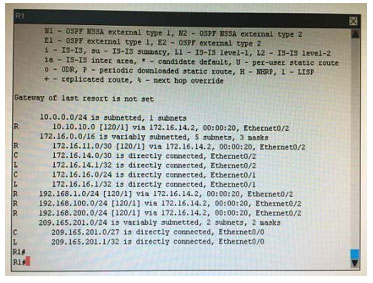
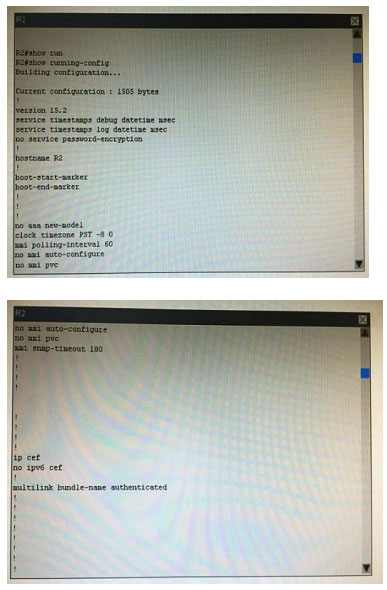
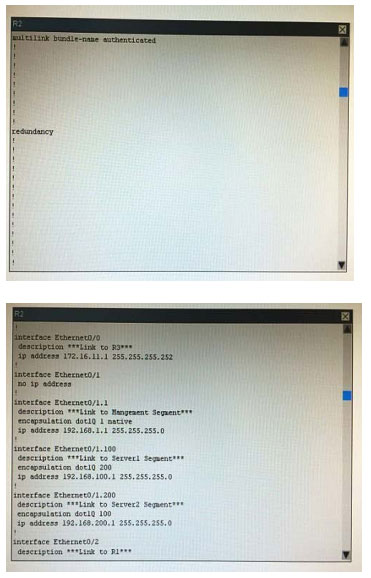
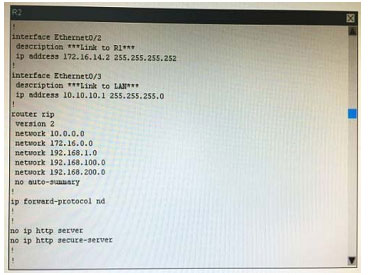
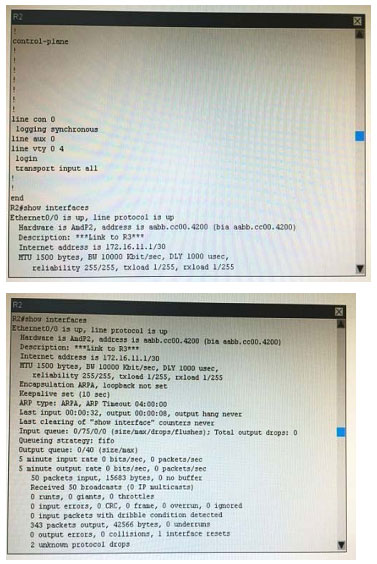
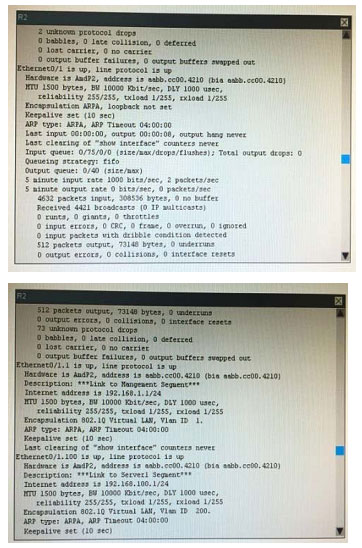
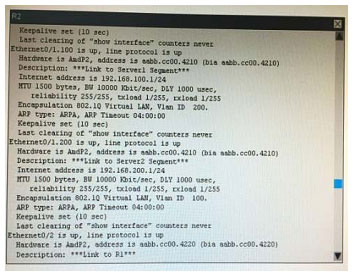

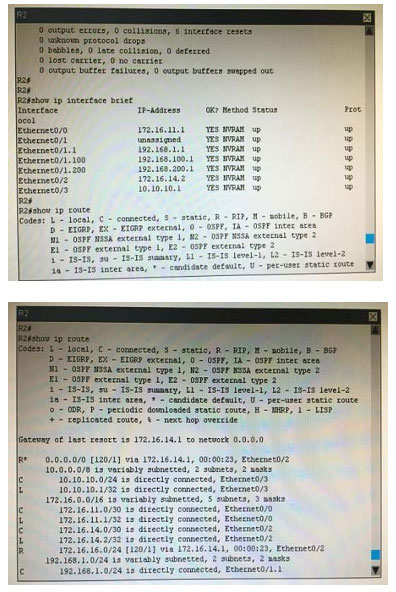
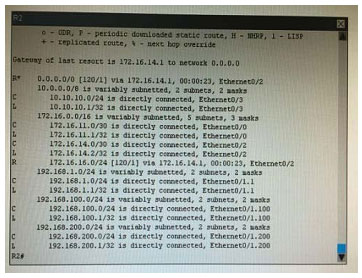
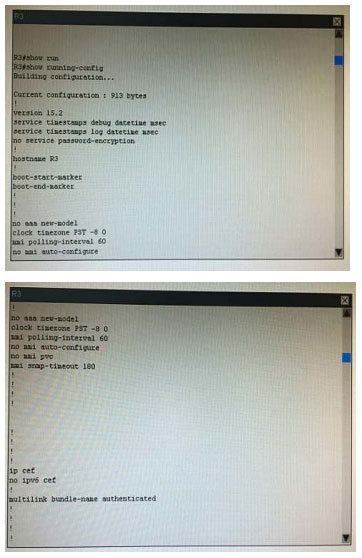
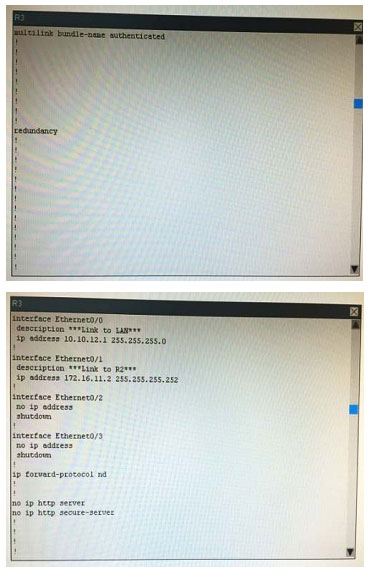
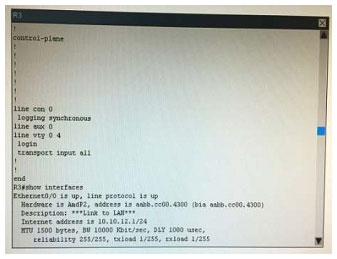
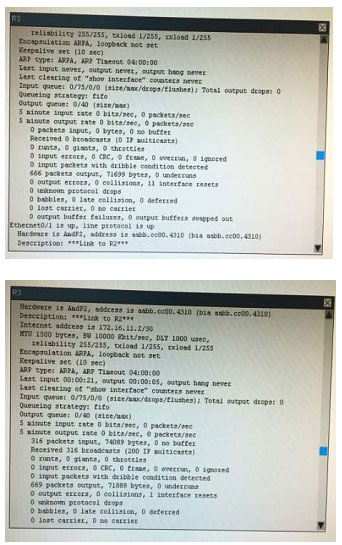
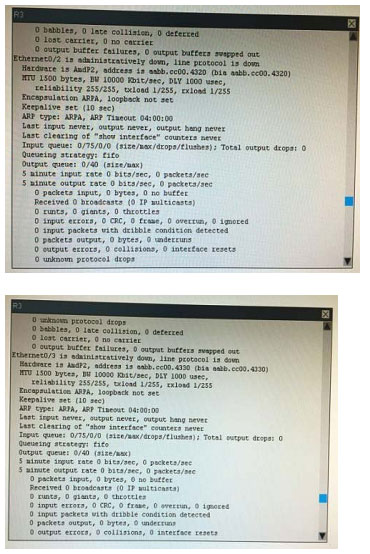
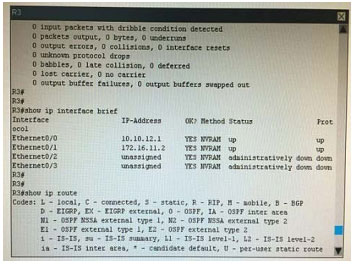

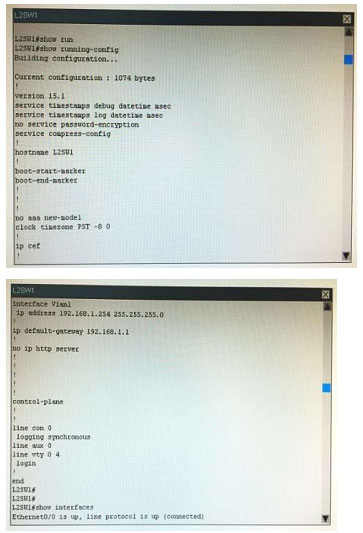
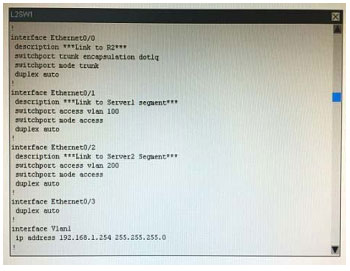
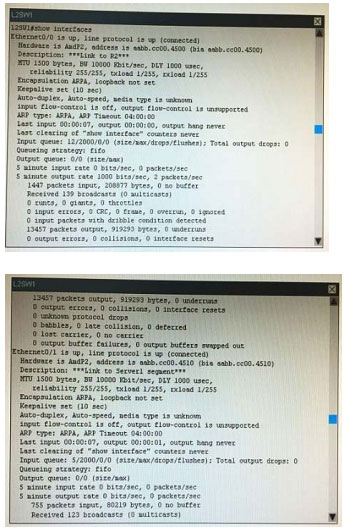
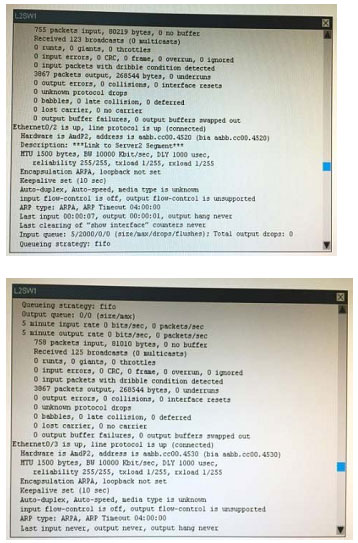
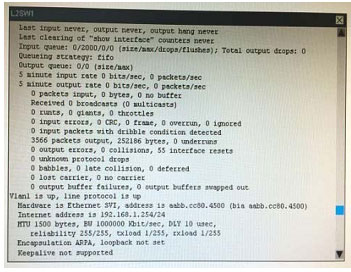
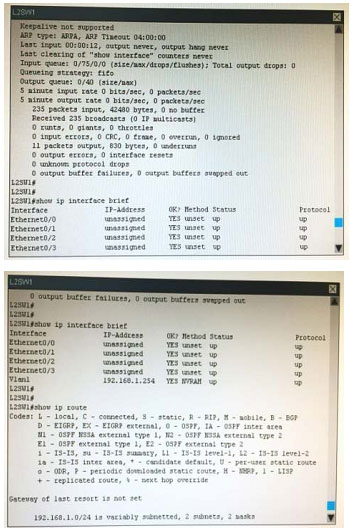
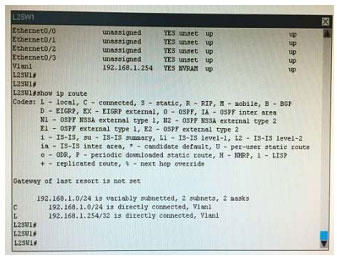
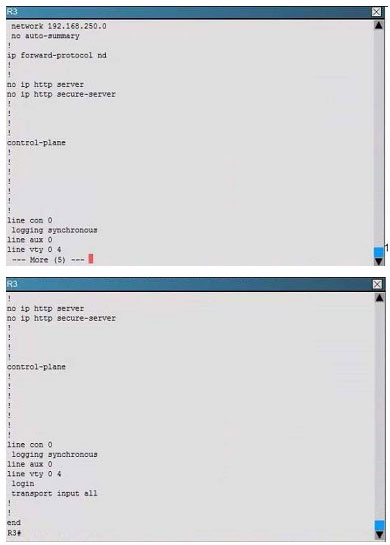
What is the correct statement below after examining the R1 routing table?
A. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses static route instead RIPv2 Because the static route AD that is configured is less than the AD of RIPv2
B. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses RIPv2 instead static route Because the static route AD that is configured is higher than the AD of RIPv2
C. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses static route instead RIPv2 But the traffic is forwarded to the ISP instead of the internal network.
D. Traffic that is destined to 10.10.10.0/24 from R1 LAN network uses RIPv2 instead static route Because the static route AD that is configured is 255
Correct Answer: B
Explanation
Explanation/Reference:
Configuration are below for the answer.

QUESTION 27
What is the maximum number of bits that can be borrowed to create subnets if a Class B network address is being used?
A. 2
B. 6
C. 8
D. 14
E. 16
Correct Answer: D
Explanation
QUESTION 28
Which NTP command configures the local device as an NTP reference clock source?
A. ntp peer
B. ntp broadcast
C. ntp master
D. ntp server
Correct Answer: D
Explanation
QUESTION 29
Which technique can you use to route IPv6 traffic over an IPv4 infrastructure?
A. NAT
B. 6to4 tunneling
C. L2TPv3
D. dual-stack
Correct Answer: B
Explanation
QUESTION 30
When you use the ping command to send ICMP messages across a network, what’s the most common request/reply pair you’ll see? (Select one answer choice)
A. Echo request and Echo reply
B. ICMP hold and ICMP send
C. ICMP request and ICMP reply
D. Echo off and Echo on
Correct Answer: A
Explanation
QUESTION 31
What happens when the cable is too long?
A. Baby Giant
B. Late collision
Correct Answer: B
Explanation
QUESTION 32
The internetwork shown in the diagram is experiencing network connectivity problems.
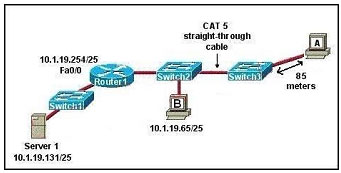
What is the cause of the problem?
A. The cabling connecting host A to Switch3 is too long.
B. The address of host B is a broadcast address.
C. The IP address of interface Fa0/0 of Router1 is not a usable address.
D. The cable connecting Switch2 and Switch3 should be a crossover.
E. The IP address of Server 1 is in the wrong subnet.
Correct Answer: D
Explanation
QUESTION 33
If NVRAM lacks boot system commands, where does the router look for the Cisco IOS by default?
A. ROM
B. RAM
C. Flash
D. bootstrap
E. startup-config
Correct Answer: C
Explanation
QUESTION 34
Which statement about unicast frame forwarding on a switch is true?
A. The TCAM table stores destination MAC addresses
B. If the destination MAC address is unknown, the frame is flooded to every port that is configured in the same VLAN except on the port that it was received on.
C. The CAM table is used to determine whether traffic is permitted or denied on a switch
D. The source address is used to determine the switch port to which a frame is forwarded
Correct Answer: B
Explanation
QUESTION 35
Which routing protocol has the smallest default administrative distance?
A. IBGP
B. OSPF
C. IS-IS
D. EIGRP
E. RIP
Correct Answer: D
Explanation
Explanation/Reference:
Explanation: http://www.cisco.com/c/en/us/support/docs/ip/border-gateway-protocol- bgp/15986-admin-distance.html
Default Distance Value TableThis table lists the administrative distance default values of the protocols that Cisco supports:
Route Source
Default Distance Values
Connected interface
Static route
Enhanced Interior Gateway Routing Protocol (EIGRP) summary route External Border Gateway Protocol (BGP)
Internal EIGRP
IGRP
OSPF
Intermediate System-to-Intermediate System (IS-IS) Routing Information Protocol (RIP)
Exterior Gateway Protocol (EGP)
On Demand Routing (ODR)
External EIGRP
Internal BGP
Unknown*
QUESTION 36
Which information is used to install the best route to a destination in IP routing table?
A. the tunnel ID
B. the prefix length
C. the interface number
D. the autonomous system
Correct Answer: B
Explanation
QUESTION 37
Refer to the exhibit.
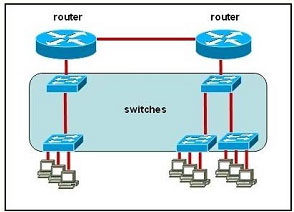
All devices attached to the network are shown. Which number of collision domains are present in this network?
A. 9
B. 3
C. 6
D. 2
E. 15
Correct Answer: E
Explanation
Explanation/Reference:
Explanation: Both switch and router separate collision domains. In other words, each port of the switch and router creates one collision domain so we have 15 collision domains in this topology.
QUESTION 38
What is the requirement of configuring 6to4 tunnelling on two routers?
A. Both ipv6 and ipv4 must be configured
B. Only IPv6
C. Only IPv4
Correct Answer: A
Explanation
QUESTION 39
Which two VLANs are reserved for system use only? (Choose two)
A. 1
B. 4095
C. 4096
D. 0
E. 1001
Correct Answer: BD
Explanation
Explanation/Reference:
Explanation: Explanation
The VLANs 0 and 4095 are reserved by the IEEE 802.1Q standard and you cannot create, delete, or modify them so they are the correct answers.
Note:
+ VLAN 0 and 4095 are reserved for system use only. You cannot see or use these VLANs.
+ VLAN 1 and VLANs 1002-1005 are default VLANs. Default VLANs are created automatically and cannot be configured or deleted by users. + VLAN 2 to 1001 are normal VLANs. You can create, use and delete them. + VLAN 1002 to 1005
are normal VLANs too but Cisco reserved for FDDI an Token Ring.
QUESTION 40
Which subnet address is for the IP address 172.19.20.23/28?
A. 172.19.20.20
B. 172.19.20.0
C. 172.19.20.32
D. 172.19.20.15
E. 172.19.20.16
Correct Answer: E
Explanation
Conclusion:
Thank you for reading, I believe that the above 40 Cisco ICND1 100-105 Exam dumps help you a lot. We insist on doing free content,
we help more people understand the network knowledge and improve your skills. We understand the importance of your time and money,
all of the above exam content from geekcert sharing, geekcert has a number of test specialists, they are trustworthy,
they have helped a lot of people pass the exam. Can’t wait to get your Cisco certificate!
Select the full 100-105 exam dumps:https://www.geekcert.com/100-105.html (Q&As:660 PDF + VCE).
[PDF] Free Cisco 100-105 dumps download from Google Drive: https://drive.google.com/open?id=1Yphc4c8ePWuVhB0QYmskoxqM_3guN6bv
[PDF] Free Full Cisco dumps download from Google Drive: https://drive.google.com/open?id=1dq6fv9FX6zSDDoHc3ge-WzVU9SNaUbsH
geekcert 15% OFF Coupon code

related:https://www.dumpkey.com/the-most-recommended-oracle-1z0-062-dumps/